Resolving a 403 Error in Aria Automation Config with vIDM Integration

The other day, I took a leap and activated the IDM integration for my Aria Automation Config instance, after months of punting it down the road and just logging in as root. Unfortunately, once I activated the integration I immediately got a 403 error once I tried to login!
Do not pass go, do not login!
Encountering a 403 error when integrating Aria Automation with Aria Automation Config using vIDM is often due to a certificate trust issue, particularly if you are using a PKI signed certificate. This guide provides detailed steps to resolve this by extracting the Root PKI certificate and adding it to the AAC server's trust store.
Step 1: Identifying the Problem
Check the log files at /var/log/raas/raas on the AAC server. If the logs indicate a certificate trust issue with the AA server's PKI signed certificate, proceed with the following steps.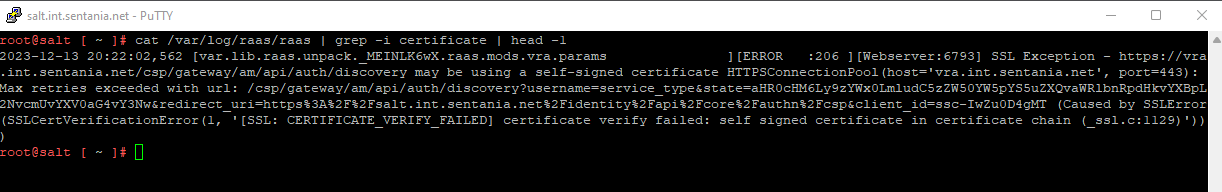
Step 2: Extracting the Root PKI Certificate Using OpenSSL
Access the AA Server and locate the certificate file.
Use OpenSSL to view the certificate chain:
1openssl s_client -connect [AA_server_address]:443 -showcertsCopy the entire Root PKI certificate, including
-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----.
Step 3: Adding the Root Certificate to the AAC Server
Transfer the Certificate to the AAC server.
On the AAC Server, copy the Root PKI certificate to
/etc/ssl/certs. Ensure the file has a.pemextension.Update the Certificate Trust Store with:
1/usr/bin/rehash_ca_certificates.sh
Step 4: Setting the Environment Variable for the RaaS Service
Update the Service File with the
sedcommand:1sed -i.bak '/ExecStart\=/iEnvironment=REQUESTS_CA_BUNDLE=/etc/pki/tls/certs/ca-bundle.crt' /usr/lib/systemd/system/raas.serviceThis inserts the
REQUESTS_CA_BUNDLEenvironment variable in the service file just before theExecStartline, it also creates a backup of the file in case you need to revert things.
Step 5: Restarting Services and Verifying the Solution
Perform a daemon reload:
1sudo systemctl daemon-reloadRestart the RaaS Service:
1sudo systemctl restart raasTest the AAC Interface to confirm the resolution of the 403 error.
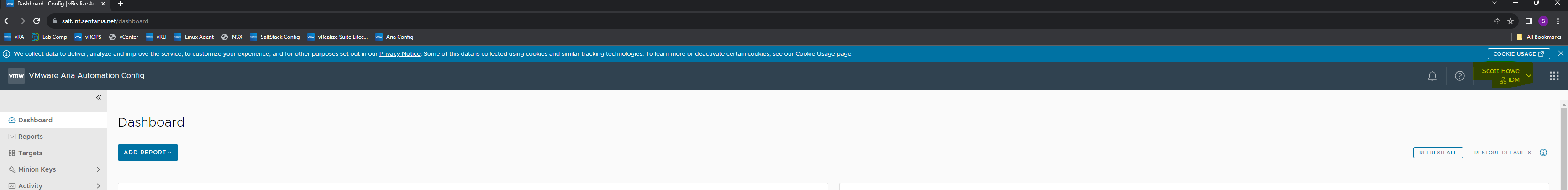
Conclusion
By following these steps, you can resolve the 403 error related to certificate trust issues in AAC when using vIDM. Remember, handling certificates and system configurations requires attention to detail to ensure secure and effective operations.